0x0002 - Safari Deleted History
cd ..Background
In a Forensic investigation it can sometimes be necessary to identify if any files have been downloaded from the internet, when they were downloaded and from which website the files were downloaded.
Apple Quarantine
A file downloaded from the Internet, has in most cases the com.apple.qurantine flag set to a specific value depending on a variety of factors.
One way to leverage this functionallity is by using mdfind in order to identify downloaded files.
Lets use the Apple Security Guidance as an example to see what attributes are set upon downloading the file with Safari.
Apple Security GuidanceMDFind
A powerful CLI Application to find files downloaded can be mdfind. Not only can it find file attributes, but it can find specific flags e.g. kMDItemWhereFroms.
mdfind "kMDItemWhereFroms == *"
xattr -l
There are multiple ways to verify the extended attributes of a file on macOS. One of which is xattr
xattr -l apple-platform-security-guide-d.pdf
Download with Firefox
com.apple.macl:
com.apple.metadata:kMDItemWhereFroms: bplist00?_;blob:resource://pdf.js/c6269054-965f-4e7b-af76-86263af16273P
com.apple.quarantine: 0081;65358134;Firefox;84790AEE-0606-4D85-A3DE-30D0C795E25E
Download with Safari
xattr -l apple-platform-security-guide-b.pdf
com.apple.quarantine: 0083;65358368;com.apple.Safari.SandboxBroker.xpc;4481BDD9-8A1A-48D3-BD8A-0304864359FD
The attribute com.apple.qurantine can be red as follows:
- Flag User allowed opening (especially relevant with installers)
- Timestamp in Hexformat
- Application which performed the download
- UUID, this can be used to find the entry in the qurantine database
~/Library/Preferences/com.apple.LaunchServices.QuarantineEventsV2
This database records the com.apple.qurantine attributes that were set. To find our two downloaded files we could execute the following sql queries:
Query
SELECT LSQuarantineEventIdentifier,
LSQuarantineAgentBundleIdentifier,
LSQuarantineAgentName,
LSQuarantineTimeStamp,
LSQuarantineOriginURLString
FROM LSQuarantineEvent
WHERE LSQuarantineEventIdentifier IS "4481BDD9-8A1A-48D3-BD8A-0304864359FD" OR LSQuarantineEventIdentifier IS "84790AEE-0606-4D85-A3DE-30D0C795E25E";
Result
| LSQuarantineEventIdentifier | LSQuarantineAgentBundleIdentifier | LSQuarantineAgentName | LSQuarantineTimeStamp | LSQuarantineOriginURLString |
|---|---|---|---|---|
| 4481BDD9-8A1A-48D3-BD8A-0304864359FD | com.apple.Safari | com.apple.Safari.SandboxBroker.xpc | 719698664.218059 | |
| 84790AEE-0606-4D85-A3DE-30D0C795E25E | org.mozilla.firefox | Firefox | 719698100.0 |
Missing Origin Attributes
We can however see, or rather not see, where the file was downloaded from. To get this information we need to get back to the file itself and us another CLI Application called mdls.
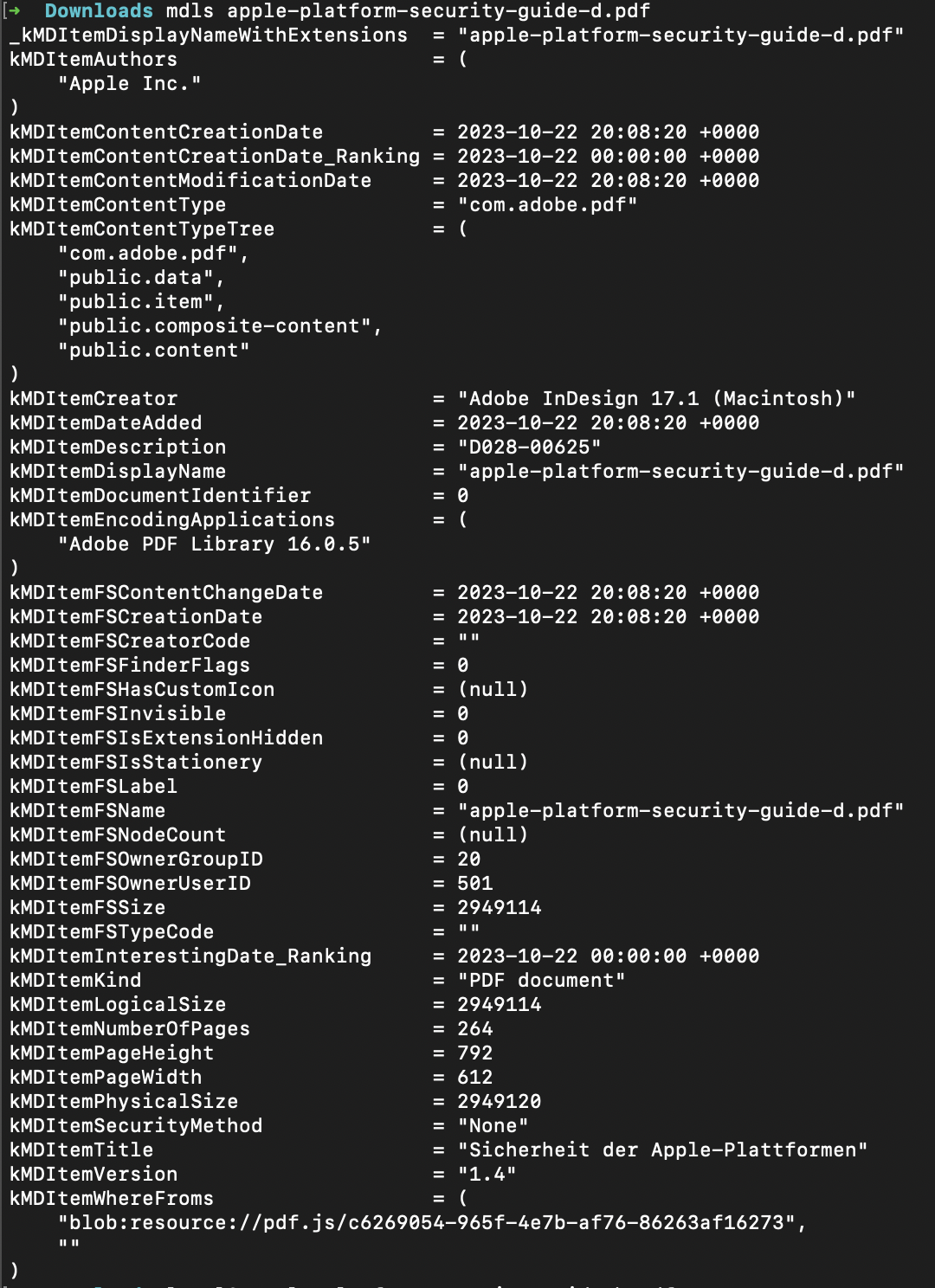
Especially interesting is the attribute kMDItemWhereFroms as it typically contains the url from which the file was downloaded.
Now that we have identified the file downloaded from the internet, lets see where we can find it in the browser History.